Cloud Computing
Cloud computing and
storage solutions provide users and enterprises with various capabilities to
store and process their data in either privately owned or third party data centers
that may be located far from the user
ranging in distance from across the world.
Cloud computing
offers several benefits for business and end users. Cloud computing is the list
of the evolution and adoption of existing technologies and paradigms. The goal
f cloud computing is allow to users to take benefit from all these technologies, without the need for technology knowledge about with each one of
them. The cloud aims to cut costs, and help to users focus on their business
instead of being impeded by IT obstacles. The main enabling technology for
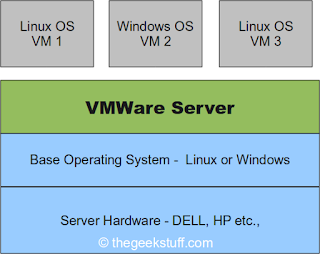
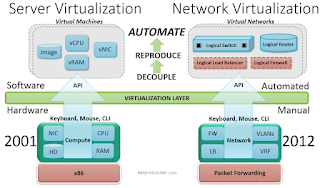
cloud computing is virtualization. With operating system level virtualization
essentially creating a scale system of multiple independent computing devices
idle computing resources can be allocated and used more efficiently.
Users routinely
facing difficult problems, Cloud computing adopts concept from service oriented architecture that can help the user break the issues into service that can be integrated to provide a solution.
Cloud computing services can be private, public and hybrid.
Private cloud is a
type of cloud computing that involves distinct and secure cloud based environment in which only the specified client can be operate. As with other
cloud models, private cloud will provide computing powers as a service within a visualized environment using an underlining pool of physical computing resource.
How ever , under the private cloud is only accessible by a single organization
providing that organization with greater control and privacy.
Public computing is a
service provider makes resources, such as application s and storage, available
to the general public over the internet.
Public cloud services may be free or offered on a pay-per-usage model. It is
easy and inexpensive setup because hardware, application and bandwidth costs
are covered by the provider and no wasted resources because you pay for what
needed use. Public cloud is a proprietary network or data center that uses
cloud computing technologies, such as virtualization.
The hybrid cloud is
combined of a public cloud provider and private could platform. That is designed
for use by a single organization. The
public and private cloud infrastructure, which operate independently of each
other, communicate over an encrypted connection, using technologies that allows
for the portability of data and applications.
Cloud computing Privacy
The service provider can access the data in the
cloud at any time. It may accidentally or
deliberately after or even delete information. Many cloud provider can share information
with third parties if necessary for the
purposes of law and order even without a warrant.Which users must agree to before
they start
Using cloud services. Solution to privacy
include policy and legislation as well as end users choices for how data
stored. Users can encrypt data that is processed or stored within the cloud to
prevent unauthorized access. Many organization bound by compels regulatory
obligations and governance standards are still hesitant to place data or
workloads in the public cloud for fear of outages, loss or theft. However the resistance is fading as logical
isolation has proven reliable and the addition of data encryption and various
identity and access management tools has improved security within the public
cloud.